Getting a little closer creating a @CiscoNetAcad #PacketTracer solution for iPad ...
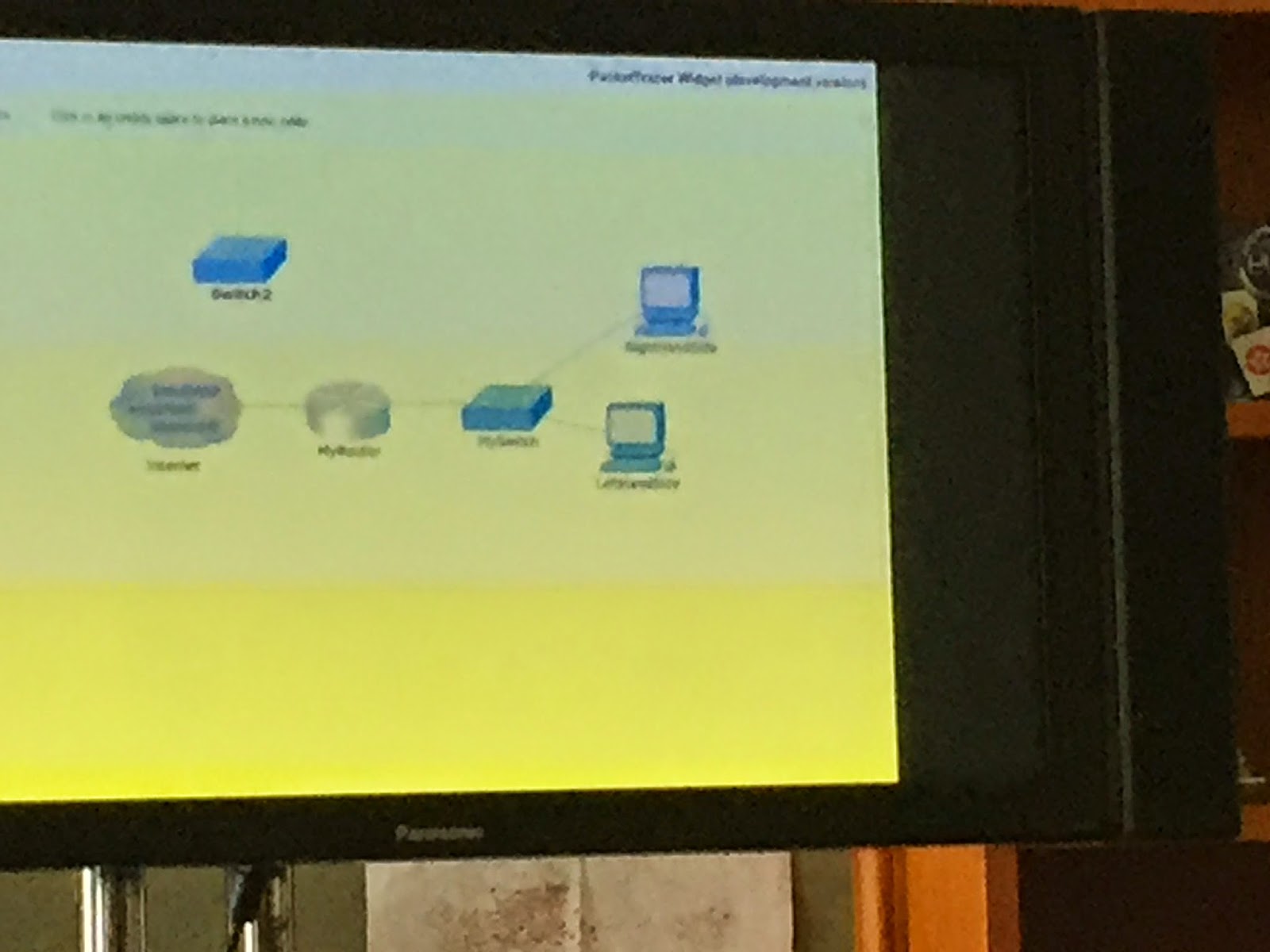
While there is much yet to be accomplished. In teaching and technical terms, I am impressed to see the work accomplished to date by colleagues within KMI at the Open University. Having found the right programmers, the project is evolving, having a working early prototype embedded within an iBook using a JavaScript front end. The affordances of a touch screen differ considerably from the typical desktop environment. Creating interfaces, adding devices, dragging/dropping are all different experiences. As well as the use of the CLI, but these are issues yet to be resolved. Forgive the quality of some of the images, we had an iPad strapped to a large flatscreen. With colleagues giving a demo to senior representatives of the Cisco Academy programme. It is still early days, however the idea has grown some legs.